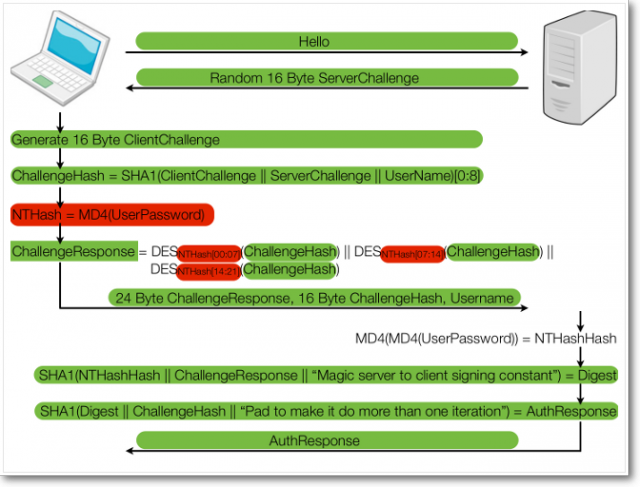
An overview of the MS-CHAPv2 used by hundreds of VPN- and WPA2-based security products.
Researchers have devised an attack against a Microsoft-developed authentication scheme that makes it trivial to break the encryption used by hundreds of anonymity and security services, including the iPredator virtual private network offered to users of The Pirate Bay.
The attack, unveiled by Moxie Marlinspike and David Hulton, takes on average just 12 hours to recover the secret key that iPredator and more than 100 other VPN and wireless products use to encrypt sensitive data. The technique, which has been folded into Marlinspike's CloudCracker service, exploits weaknesses in version 2 of a Microsoft technology known as MS-CHAP, short for Microsoft challenge-handshake authentication protocol. It's widely used to log users into VPN and WPA2 networks and is built into a variety of operating systems, including Windows and Ubuntu.
"We hope that by making this service available, we can effectively end the use of MS-CHAPv2 on the Internet once and for all," the researchers wrote in a blog post published over the weekend. "We find many popular VPN products are susceptible to a variety of practical user deanonymization attacks. Weaknesses stem from lack of security analysis of the composition of VPNs, applications, and the TCP/IP stack on each respective operating system."
Read 11 remaining paragraphs | Comments
No comments:
Post a Comment